Proxy Support
If you have a dedicated proxy between your SCOM Management servers and your ServiceNow instances you will need to configure a proxy. The ServiceNow connector picks up your proxy settings from "Internet Options" configured on your server in most cases (see here for a how-to guide).
Specific proxy settings
Added in 1.3.1.4221
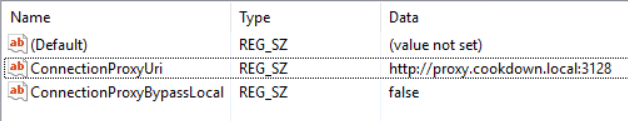
In some cases, Alert sync and Discovery need to have their own proxy settings defined. These are set in the registry of each SCOM Management Server (if your Resource Pool contains multiple servers, you will need to configure this on each server in the pool) and are not present by default.
KEY: HKEY_LOCAL_MACHINE\SOFTWARE\CookdownManagementPacks\AlertSync
KEY: HKEY_LOCAL_MACHINE\SOFTWARE\CookdownManagementPacks\Discovery
Values:
ConnectionProxyUri – the URI of the proxy to connect to
ConnectionProxyBypassLocal – Optional, defaults to false, used when creating the proxy
PortProxy configuration
Added in 1.6.0.1
You may already have an edge server/network device that has the ability to connect out to your ServiceNow instance. A computer hosting a ServiceNow Mid Server for example. You can implement a port proxy on a single port to enable one or more management servers to communicate to your instance, negating the need to implement or interface with a dedicated proxy server.
In our fictitious examples, we will use:
A Windows server with an IP address of 10.10.0.55and a DNS name of infra-mid01.companyinc.local that we will use to host a portproxy.
A Linux server with no further defined attributes that we will use to host a portproxy.
A pair of SCOM Management servers with IP addresses of 10.7.0.80 and 10.7.0.81.
A service now instance at https://companyincsandbox.service-now.com.
The examples focus on Windows and Linux servers, however other port proxy implementations should also work.
Configuring portproxy on Windows using netsh
See also: Microsoft’s documentation for netsh interface portproxy
The following command sets up your Windows server to listen on 10.10.0.55:22000 and direct the traffic to cookdown.service-now.com:443. This can be run from an elevated command prompt or PowerShell instance.
netsh interface portproxy add v4tov4 listenport=22000 listenaddress=10.10.0.55 connectport=443 connectaddress=cookdowndev.service-now.com
Next, we need to configure the local firewall to accept connections from the management server. In this example, we will open up the port to a pair of management servers using PowerShell.
New-NetFirewallRule -DisplayName 'Portproxy for SCOM to ServiceNow' -Enabled True -Direction Inbound -Action Allow -RemoteAddress '10.7.0.80','10.7.0.81' -Protocol TCP -LocalPort 22000
Configuring port proxy on Linux using FirewallD
See also: Red Hats documentation for rich rules
The following command sets up a Linux server to accept connections from a management server on port 51000 and direct the traffic to the IP address of our ServiceNow instance. At the time of writing FirewallD does not support the use of hostnames in this capacity.
firewall-cmd --add-rich-rule='rule family="ipv4" source address="10.7.0.80" forward-port to-addr="149.96.5.119" to-port="443" protocol="tcp" port="51000"'
The following Ansible playbook uses the firewalld module to set up a Linux server to do the same for the other management server using optional additional logging.
---
- hosts: portproxy
become: true
tasks:
- name: Redirect port 51000 to 443 ServiceNow with rich rule
firewalld:
rich_rule: rule family=ipv4 source address=10.7.0.81 forward-port to-addr=149.96.5.119 to-port=443 protocol=tcp port=51000 log prefix="SCOM-portproxy" level=info
permanent: yes
immediate: yes
state: enabled
...
Apply the registry keys to enable the host header override
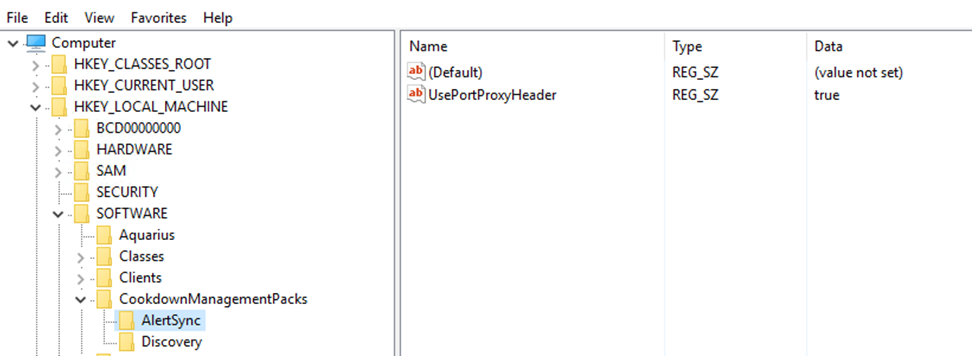
ServiceNow requires the host header on the request to match the instance name (not your internal port proxy server). We enable this using a string registry value 'UsePortProxyHeader' on each management server in the Cookdown resource pool.
KEY: HKEY_LOCAL_MACHINE\SOFTWARE\CookdownManagementPacks\AlertSync
KEY: HKEY_LOCAL_MACHINE\SOFTWARE\CookdownManagementPacks\Discovery
Value:
UsePortProxyHeader - String set to true
'AlertSync','Discovery' | Foreach {
$Path = "HKLM:SOFTWARE\CookdownManagementPacks\$_"
If (-not (Test-Path -Path $Path)) {
New-Item -Path $Path -Force
}
#Check to see if the Key exists, if not create it and any missing parent keys.
New-ItemProperty -Path $Path -Name 'UsePortProxyHeader' -PropertyType String -Value 'true' -Force
#Create new string value, overwriting if it exists already.
}
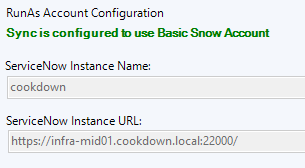
Updating the ServiceNow connector to point to the port proxy
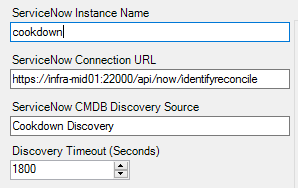
Both AlertSync and Discovery configurations need to be pointed at the newly opened port proxy address using the IP or DNS name of the server hosting the port proxy. Make sure to keep the rest of the URL the same and only change the host portion. The ServiceNow instance name must be set to the destination instance.
You should now be ready to use and test the port proxy.